5-steps to automate the supervision process

A step-by-step guide for automating the supervision process for monitoring compliance and customer experience.
- Are you ready to automate your manual compliance monitoring?
- Does your current supervision involves manual listening of hours of calls and reviewing communication logs?
- Have you received a regulatory investigation request for a significant compliance breach and are not sure where to start?
- Do you have customer complaints and need to better understand customer concerns and sentiments?
We're talking about setting up efficient supervision processes with automation, significant cost savings, huge customer experience gain, and risk reduction.
Below are the 5- key steps for setting up an automated incident reporting
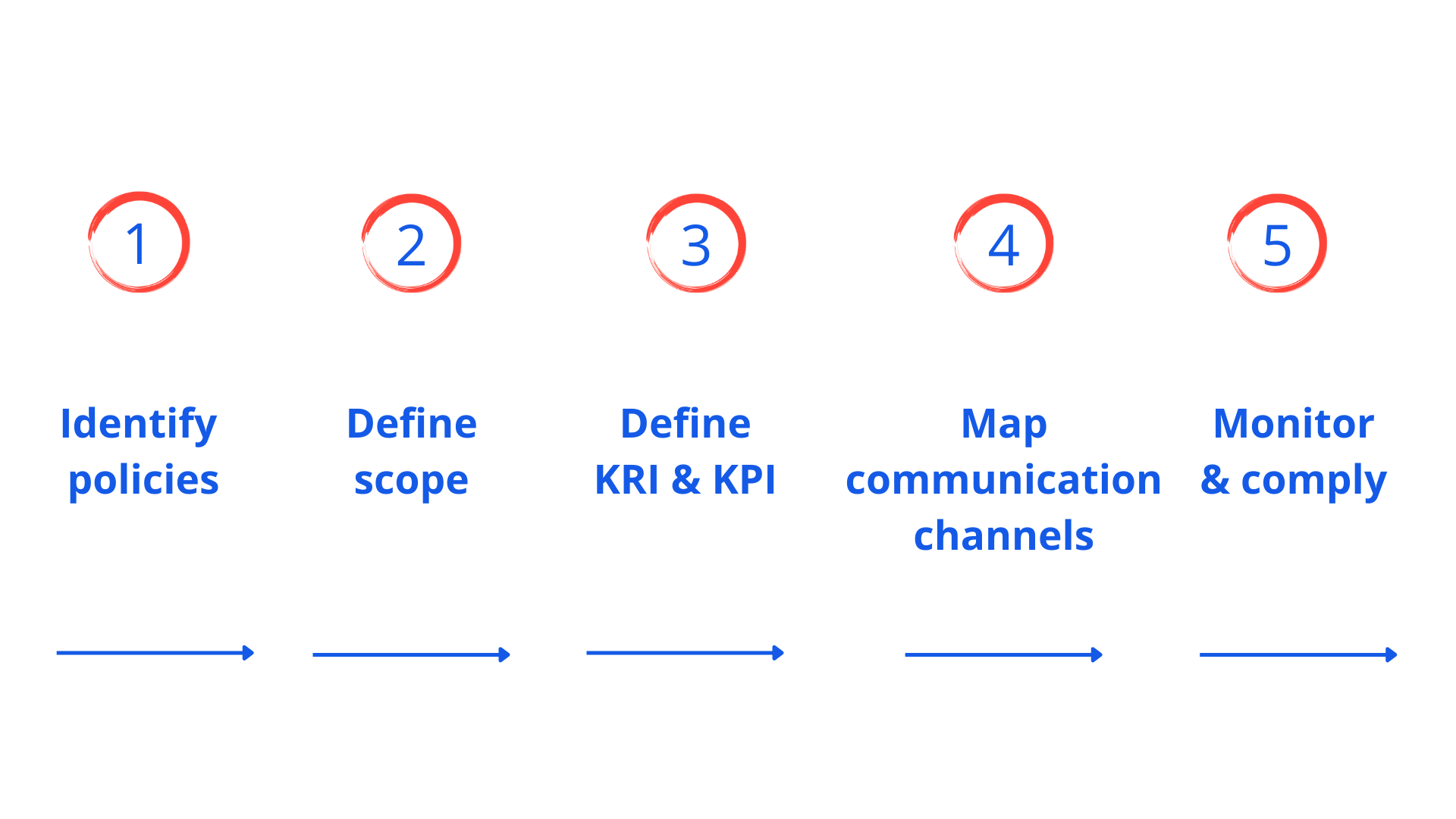
Step 1: Identify policies
Most regulated firms usually have documented quality assurance systems that include: roles and responsibilities; pre-defined procedures for identifying, assessing, and understanding each of the quality, compliance issues, and material risks to capture operational issues.
It is usually documented as a QA scoring spreadsheet for quality assurance and compliance similar to the below format.

Supervisors manually listen to hundreds of hours of phone calls and score each conversation against quality, customer experience, and compliance requirements.
The first step here is to bring some of these requirements to a standard format in the form of policies that is easy to maintain across the organization and set up governance standards for the supervision process.
Mapping the requirements to a policy-based standard format
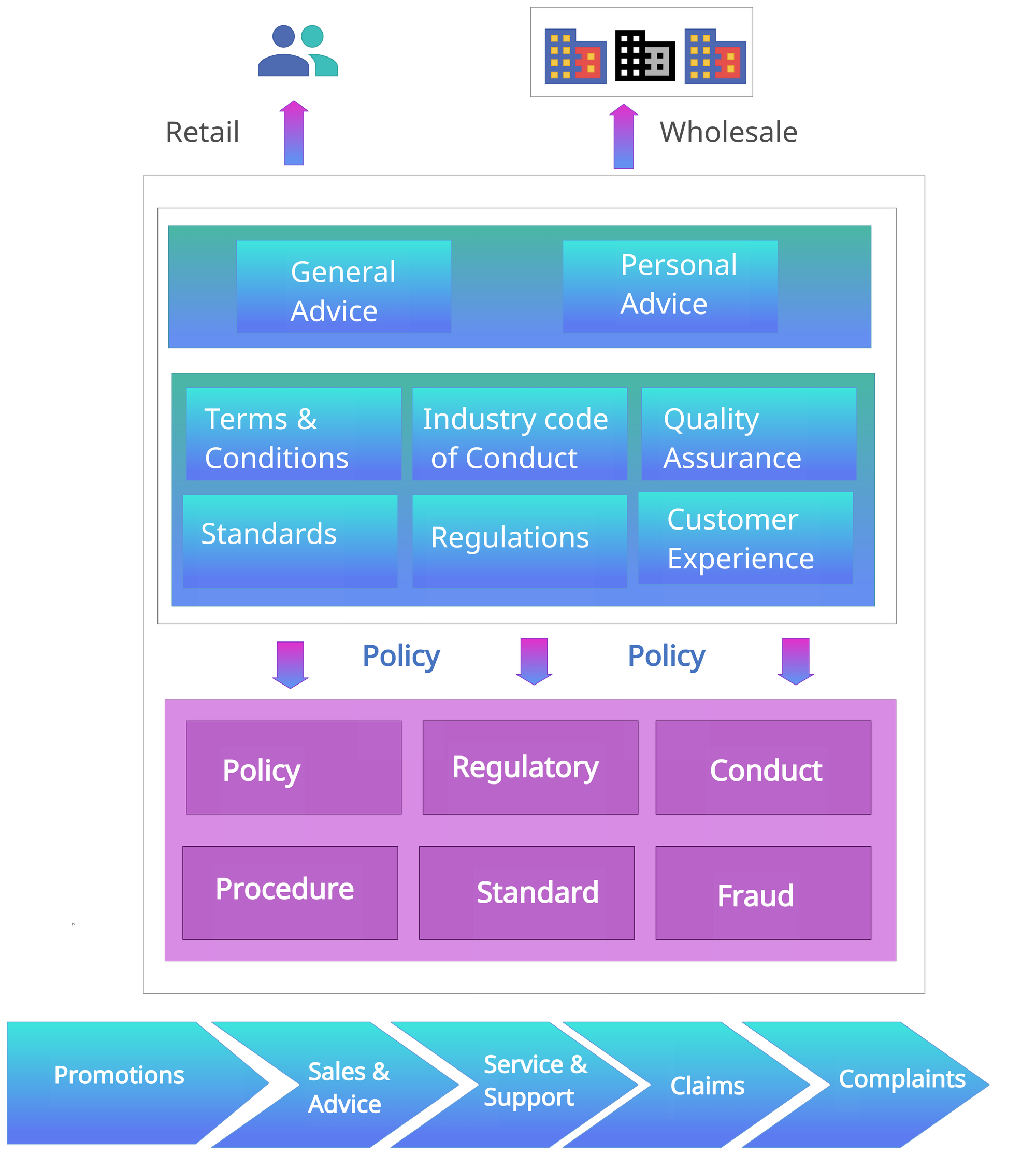
Map each of the requirements to policy type. For example, all legal requirements fit into the regulatory policy type. Any product T&C or disclosure requirements can fit into the procedure or default policy option.
Standardizing policies makes it easier to manage incidents and set up action plans around them.
Step 2: Define the scope
This step requires mapping each policy with the business objective and scope.
This ensures that business policies are associated with geography, business unit, product, and processes. It supports adequate oversight of the incident management systems by risk/compliance, operational, and board of governance functions, and supports clear reporting.
Step 3: Define KRI & KPI
Performance criteria need to be defined with two key sets of criteria
- KRI for policies to support a risk-based supervision model
- KPI to support a customer-centric approach
Every policy is different and needs to be prioritized differently based on the responsible entity’s risk appetite and the risk tolerance for each material risk identified.
Risk-based supervision is a structured process and approach that identifies the most critical risks faced by the regulated entity. In contrast to a tick-box-based approach, each policy will be prioritized based on the fines, reputational damage, customer detriment, and cultural aspects.
A customer-centric approach is a way of doing business that fosters a positive customer experience at every customer journey stage. It builds on customer loyalty and satisfaction, which leads to referrals for more customers.
What customer experience metrics or KPIs can be measured?
- First call resolution, NPS
- Customer sentiment and tone
- Concerns and complaints
- Automated scorecard for overall customer experience
Step 4: Map communication channels
For effective supervision, monitoring should be looked beyond just the contact center and all communication channels need to be identified for each of the policies.
Customers want you to use the channels they’re most comfortable with, from phone calls to web chat, SMS, email, and social media. They expect a seamless experience across all of them.
An omnichannel solution allows agents to handle requests and share information across multiple channels, including phone calls, webchat, email, SMS, and social media.
Post-pandemic hybrid work has become mainstream. With most communication happening through text or video calls, this leads to massive data build-up and challenges in supervision. This creates a huge challenge in the tracking of employee activities, and goals.
Step 5: Monitor & comply
The result of the monitoring is an incident and breach reporting system. Firms can classify incidents or breaches depending on the severity, risk classification, and internal and regulatory reporting requirements.
The incident and breach register need to ensure there is a clear action plan defined and set up for the incident and breach management. For example,
- How frequently does it need to be monitored?
- What happens when there is an incident or breach is reported?
- Who gets notified and how often?
- What are the actionable insights?
- What are the remediation actions and follow on reporting?
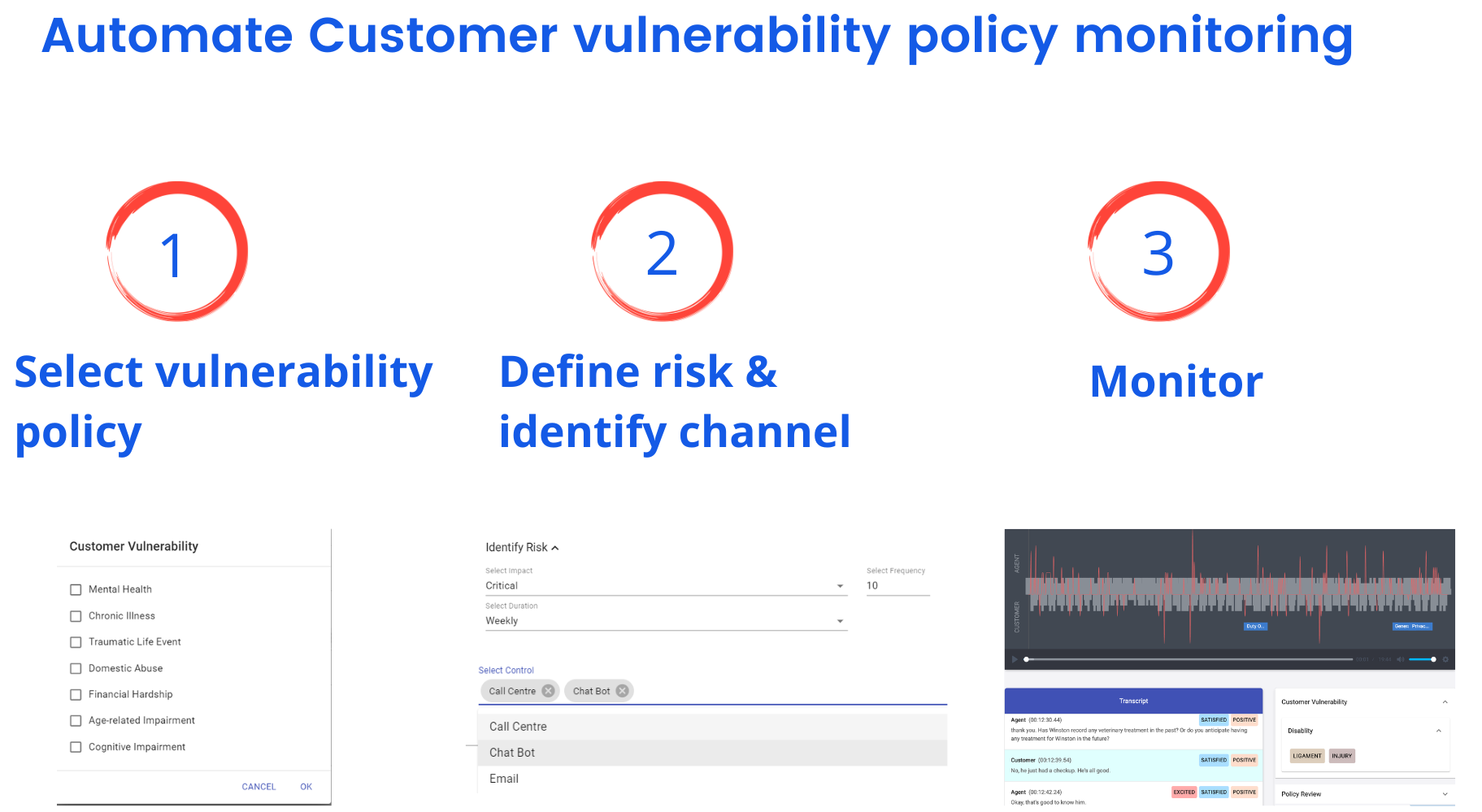
Below is an example of how a customer vulnerability policy can be monitored to support financial inclusivity. Understanding what aspects of customer vulnerability need to be monitored is the first step.
The key takeaways
So, before setting up an incident management system to automate the supervision process, keep in mind these five tips:
- Make sure all your supervision requirements refer to a common standard and policy-driven
- Don't put all policies in the same bucket and prioritize policies based on the risk threshold
- Omni-channel and hybrid work is here, so think beyond the contact center
- The system should give actionable insights and set existing supervisors free from repetitive mundane tasks. Now supervisors can focus on operational performance and customer experience review and optimization.
